Back
The Essential Penetration Test Report Template

You're not alone if you struggle to understand a pen test report beyond the executive summary. Chances are, you’ve gone through your share of pen tests and sifted through the resulting reports, most of which follow repetitive templates that easily stretch past 100 pages.
In many cases, pentesters dedicate up to 60% of the time they spend testing to preparing the report, no matter how skilled or experienced they are. Clear, actionable insights from penetration testing reports are more critical than ever. Yet, pen testing reports are, more often than not, fluffy, dense, and hard to digest.
How should you prioritize your effort, communicate the urgency within the company, or act on remediation steps if you can’t pinpoint them or connect them to your business context? This lack of clarity can change once you understand what a pen testing report should look like and can communicate the structure you expect from your internal team or external testers.
What is a Penetration Test Report and Why Does it Matter?
A penetration test report is a detailed document that outlines the findings of a penetration test. Whether it’s a manual or AI-driven pen test, most reports follow the same structure: an executive summary, scope and methodology, a section on vulnerabilities/exploits found with remediation, and compliance mapping (more on this below!).
The report could have a different focus depending on the reasons for testing. A lot of pen tests are done primarily for compliance purposes. Some are done solely for remediation, and some as proof of work by the security or compliance team to the board, compliance editor, a customer, or partner. The problem is that in most cases, no matter the format and reason, the company you hired wants to give you a feeling that you’re getting your money’s worth, so they make the report unnecessarily extensive. Sadly, often the time spent on an unnecessarily extensive report comes at the expense of time spent on a deeper and wider test.
The result is often a repetitive report that could be full of fluff and jargon, lacking business context, non-actionable information, and generic vulnerability scoring and remediation descriptions. In reality, each environment and application is different and thus requires context-specific and tailor-made reporting and remediation steps.
A valuable report should weave business context into every section, from the testing methodology and attack surfaces covered to the roles assessed, vulnerabilities identified, and how severity and prioritization are determined. A CVSS score alone isn’t enough. You need insights that reflect real-world stakes: internal policies, potential financial losses, stock price impact, relevant industry breach comparisons, and other tangible business implications. This should be a requirement when selecting a pentest vendor.
In the remediation section, it’s critical to include evidence of exploitability, the likelihood of success (based on complexity and feasibility), and the most straightforward way to disrupt the attack chain. Prioritization and language throughout the report should be tailored to resonate with various stakeholders, making it easy to act on.
That means using role-appropriate terminology and KPIs that require minimal explanations, whether the reader is a developer, a CISO team member, someone from finance, legal, or even the board of directors.
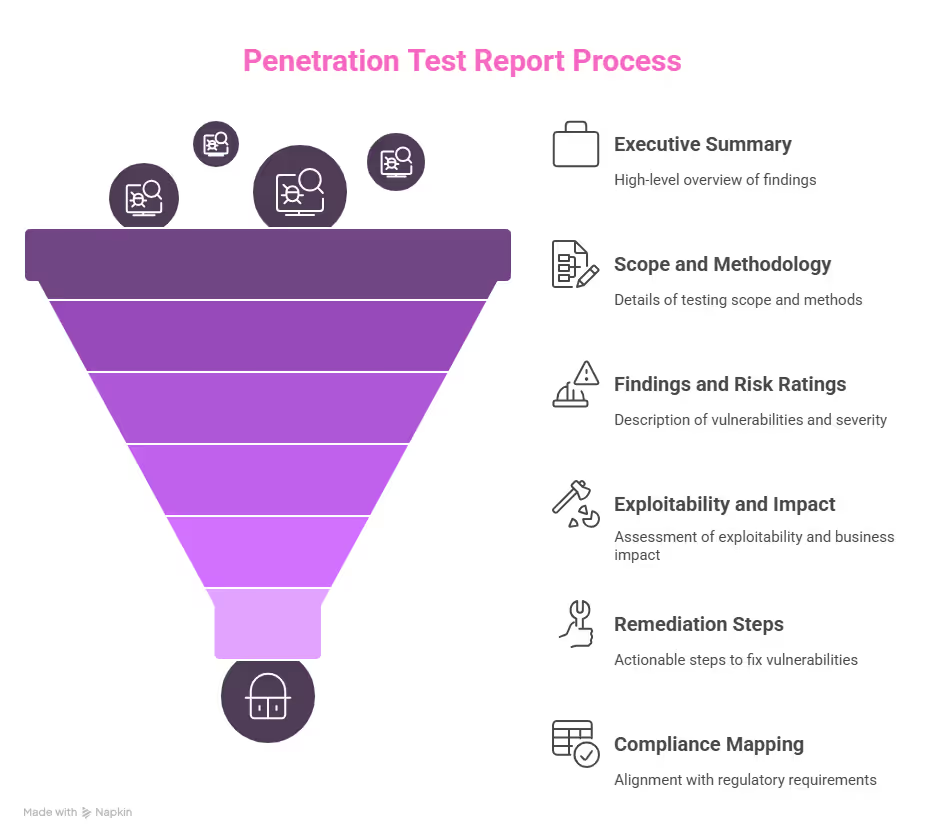
The Standard Structure of an Effective Penetration Test Report
1. Executive Summary
This section includes a high-level overview of the findings and explains the vulnerabilities identified and their potential impact on the organization. If there are any significant compliance issues, they’d likely be presented here as well.
2. Scope and Methodology
This section includes the details on the systems, architecture, apps, and attack surfaces covered in the test. Usually, it’s a rehash or copy of the testing scope agreed upon before testing. Similarly, this section would include the testing methods, limitations (such as time limits or apps that were out of scope), and whether critical access management components, like IAM tools, were evaluated.
3. Findings and Risk Ratings
This section includes a description of each vulnerability discovered, usually with its official CVSS name, severity level, and potential impact, if available. Each vulnerability description would also include proof of exploitability and explain each step taken.
4. Exploitability and Business Impact
This section evaluates how easily a vulnerability can be exploited and the potential impact. It considers the attacker’s required skill level, dependencies, tools or techniques, and the likelihood of a successful breach. Each vulnerability should also be framed in a business context, such as exposure of sensitive data, financial losses (equipment replacement, loss of income, theft, or stock price drop), service disruptions (like ransomware), and possible legal consequences.
5. Remediation Steps and Recommendations
This section includes actionable steps to remediate the identified vulnerabilities and a subsection on improving the security posture. If there are general development, security, or infrastructure recommendations, they would also be included here.
6. Compliance Mapping
This section outlines how the identified vulnerabilities relate to specific compliance requirements. Based on the requirements, it details whether the company meets, partially meets, or fails to meet each relevant requirement. This section can be used as the ‘stamp of approval’ to prove compliance.
Breakdown of the Essential Penetration Test Report Template
While we provide an overview of what a pen test report should look like in this section, you can download our complete PDF template to see what a simplified pen test report looks like. This format makes it easier to cross-reference and filter information by various metrics.
You can use this report for remediation and compliance. However, following a continuous penetration testing practice, you can also use it to keep up with the pace of change and track your vulnerability remediation efforts and the number of vulnerabilities across different app versions over time. Overall, the report might look like the ‘standard’ report discussed earlier, but with a few key nuances:
1. Integrated Business Context
The same vulnerability, if exploited, would affect each company differently. Each company has different stakes, such that the potential loss cannot be explained or estimated without understanding its context. The business context in this case involves various elements, including:
- The compliance frameworks that the company has to adhere to
- The type of information the company keeps
- The potential fallout if the data gets out
- The kind of clients the company serves
Since the potential results vary so greatly, the decision on prioritizing remediation can not be made without this information. Instead of relying on the organization undergoing the test to assess and add context to each vulnerability, it’s much more effective and valuable if the penetration testers themselves include this information. After all, this context should also impact how the test is conducted and the type of breaches the testers try to emulate.
2. Compliance Tracker
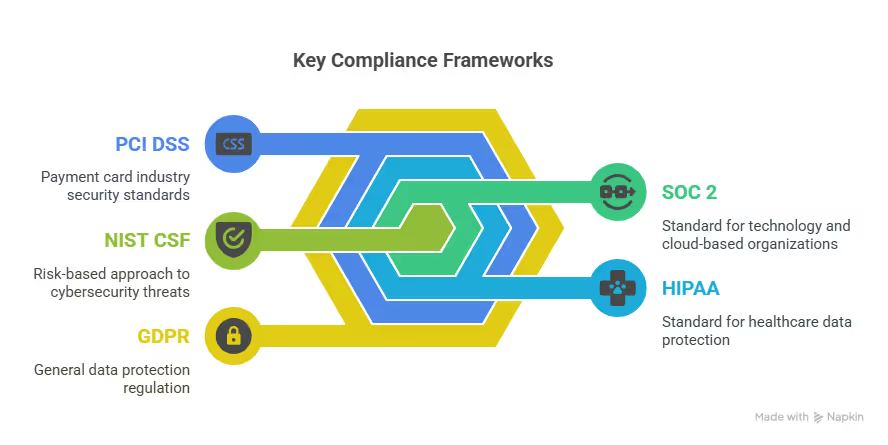
Although a pentest is a strong and vital security checkpoint, it is also often used for compliance. Consider aligning with several regulatory and cybersecurity frameworks. Starting points include SOC 2 and ISO 27001, HIPAA, PCI DSS, and GDPR, to name a few more prominent ones. Depending on which framework accreditation you seek, it’s helpful to see clearly and graphically the required steps or missing elements to complete your compliance requirements. Each required framework should be listed separately for clarity, even though they may have some requirements in common.
3. Uniform Language and Inter-Report Links
Each vulnerability and exploit should have the same name and identifier across all sections. Each section should be cross-linked to all the others so that you don’t need to start flipping through sections to look for something specific that happens to be in a different location than the one you’re in. Since we’re no longer handing in printed reports, there is no excuse for making it harder for the readers to find the information they want.
4. Relevant Personas Section for Each Vulnerability
Rather than leaving it up to the reader to guess who needs to be informed about a vulnerability and why, each vulnerability should include a list of relevant personas in the recommendations section. Each persona should have a tailored explanation, highlighting why it matters to them and what actions they might take to help address the issue.
Incorporating application dependency mapping in this section allows you to identify which personas are tied to specific applications and systems, highlighting how their vulnerabilities might impact their areas of responsibility.
This report shouldn’t be presented just as a PDF. Instead, it should be a dashboard that should be constantly updated and can be filtered by persona so that each relevant person can see exactly what they need to handle and nothing else.
5. Editable Action Items for Remediation Planning
It’s sometimes easy for those preparing the report to forget that the remediation and prioritization they suggest are just that - suggestions. The remediation suggestion should be prioritized based on the unique business context and the potential business harm, not just a CVSS score. It makes more sense to have an editable section that allows stakeholders across departments to coordinate, adjust priorities based on internal context, and collectively plan the remediation effort.
For example, the report could include fields like:
- Severity level: Informative/Low/Medium/High
- Proof of Exploitability: V/X
- Business Impact: Low/Medium/High/Critical
- Comparable Breaches Damage: In $$$
- Reaches Critical Assets: Yes/No
- Exploit Complexity: Low/Medium/High
- Remediation Complexity: Low/Medium/High
This framework ensures that the vulnerability prioritization reflects the potential harm to the business, considering more than just the technical aspects of the vulnerability, but also its potential financial and operational impact.
How to Maximize the Impact of Your Penetration Test Reports
A typical report has too much fluff and jargon to be effective. Vulnerability prioritization is usually derived from the standard scoring systems (CVSS and EPSS), with no regard for real-life risk-based prioritization. Finally, almost all reports are static, representing a point-in-time sample and quickly obsolete once any software update occurs, which lately happens more often than ever, with less control.
Solutions like Terra, which use Agentic AI for both pen testing and report preparation, offer context-aware, continuously updated reports that align with real-world attack scenarios. However, even with the best report possible, you still need to work to maximize the potential benefits.
Terra integrates report production with your CI/CD pipeline. Each new software version is re-tested, and a new, updated report is produced. This continuous reporting keeps the vulnerability lists up-to-date for the security department's remediation orchestration, while the compliance department can export its required static reports.
Since new vulnerabilities and exploit discoveries accelerate, keeping your defenses up-to-date is imperative. For example, the critical ConnectWise ScreenConnect Authentication Bypass Vulnerability (AKA CVE-2024-1708, CVE-2024-1709), disclosed on February 13th, 2024, could affect tens of thousands of ScreenConnect users. The vulnerability, offering an easy authentication bypass to gain admin privileges, saw real-world attacks within days of the initial report.
It’s the pen tester’s job to stay on top of the latest vulnerability and exploit databases, but that effort could be meaningless if your pen tests are too infrequent. Besides keeping reports and remediation regular and up to date, you need to keep them relevant. Agentic pen testing tools like Terra keep the attack surfaces and vulnerabilities tested, context-aware, and linked to business logic and data flow.
You probably wouldn’t care about remediating a vulnerability that has no business impact, no matter how severe it is in theory. Since every architecture and app is unique, you want the test and report to be as custom-tailored to your business as possible.
A Case in Point for a Well-Composed Report
A practical report details business implications in every section. It explains the business context of the testing methodology (including attack surfaces and vulnerabilities tested), the scope of the assessment, and the user roles tested. Prioritization and language should be clear and tailored to every potentially relevant stakeholder across the organization.
Terra’s ability to offer an Agentic-AI continuous testing and reporting over an easy-to-understand and integrated template gives you a clear advantage. You can prioritize remediation effectively and gain inter-departmental clarity, making security a cross-company effort.
Download our Penetration Test Report Template to see how revolutionary a clear and understandable pen test report could be for your pen testing program.
Be the first to experience the future of security.
Secure your spot by leaving your email








