Back
What is Offensive Cybersecurity (OffSec)? Benefits, Examples, and Best Practices
%20What%20is%20offensive%20cyber%20security%20(OffSec)_%20Benefits%2C%20Examples%2C%20and%20Best%20Practices.avif)
Most enterprise security programs are built to defend. Firewalls, SIEMs, intrusion detection systems, and compliance audits are designed to detect, block, or respond to threats. But they all share a fundamental limitation: they operate reactively, focusing on known attack patterns and post-exploit signals.
72% of organizations report increased organizational cyber risks, with nearly half citing adversarial generative AI as their primary concern. These AI-enabled attack techniques can rapidly identify non-obvious weaknesses, such as logic flaws, misconfigurations introduced during rapid deployments, and complex exploit chains that static scanners often miss.
Offensive security is one way to proactively hunt for these weaknesses by emulating the tactics, techniques, and procedures attackers now use.
What Is Offensive Cybersecurity?
Offensive cybersecurity (often abbreviated as OffSec) refers to actively probing systems, applications, and infrastructure to identify and exploit vulnerabilities before adversaries do. It goes beyond traditional security monitoring by simulating real-world attack scenarios to uncover exploitable weaknesses across an organization’s digital environment, including applications, networks, APIs, business logic flows, and software supply chains.
Unlike defensive strategies that focus on protection and mitigation, offensive security aims to test the limits of those defenses. The goal is to expose risks in a controlled, ethical manner before malicious actors can exploit them in the wild.
Who Performs Offensive Cybersecurity?
Typically, OffSec engagements are led by professional service providers, penetration testing as a service (PTaaS) providers, internal ethical hackers, and red team operators. These individuals mimic adversary behavior using manual tactics, automation tools, or a combination of both. AI-powered tools and hybrid platforms are increasingly used to scale these capabilities across larger attack surfaces.
The Offensive Cybersecurity Lifecycle
A comprehensive OffSec program typically follows a structured path:
- Scoping: This phase outlines what systems we'll be looking at, how we'll test them, and when the testing will happen. We'll also agree on how we'll communicate and handle any issues.
- Reconnaissance: This phase focuses on gathering intelligence about the target’s infrastructure, such as IP ranges, open ports, and technology stacks.
- Threat Modeling: Here, the goal is to assess which attack paths are most plausible by analyzing the system’s architecture, data flow, and business-critical operations.
- Exploitation: This involves actively testing identified weaknesses, such as insecure APIs, outdated software, improper access controls, etc., to gain unauthorized access or execute malicious actions.
- Post-Exploitation: After gaining access, pen testers demonstrate the practical consequences of a breach, such as accessing sensitive data, impersonating users, or escalating privileges.
- Reporting & Remediation: Findings are compiled into actionable reports that prioritize issues based on exploitability and business impact.
Teams can apply this lifecycle through various operational models, from point-in-time penetration tests focused on a specific release to continuous penetration testing embedded in the development pipeline.
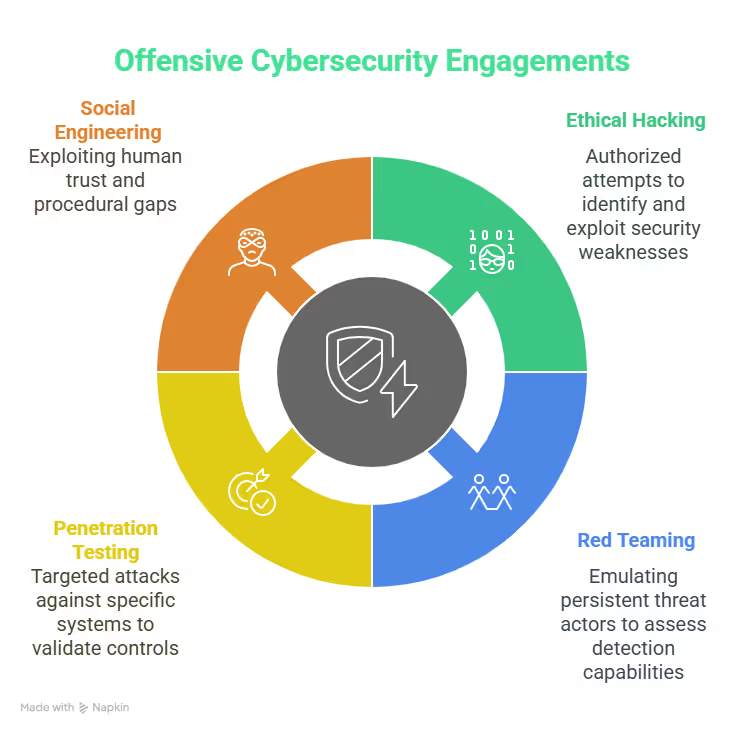
Types of Offensive Cybersecurity Engagements
1. Ethical Hacking
Ethical hacking is a broader term that includes any authorized attempt to identify and exploit security weaknesses. It spans a range of engagements, from pen tests and red teaming to API fuzzing and application or mobile testing. Ethical hackers help organizations move beyond compliance by surfacing real-world risks that generic assessments miss.
2. Red Teaming
Red teaming emulates persistent, stealthy threat actors across multiple attack phases, from initial access to post-exploitation. These simulations often assess real-world detection and response capabilities without alerting the blue team. They reveal blind spots in SOC workflows, lateral movement paths, and response gaps under realistic conditions.
3. Penetration Testing (Pen Testing)
Penetration testing simulates targeted attacks against specific systems such as web apps, APIs, or internal networks. Typically scoped and time-bound, an external penetration test validates technical controls and uncovers security flaws missed by scanners. When conducted in a white or grey-box context, it provides deeper insights into business logic weaknesses and serves compliance and risk-reduction objectives.
4. Social Engineering
Social engineering assessments target the human element of security, using tactics like phishing, pretexting, and impersonation to exploit trust and procedural gaps. These engagements test employee awareness, incident reporting processes, and the organization’s ability to contain attacks that bypass technical controls.
4 Strategic Benefits of Offensive Cybersecurity
1. Identifies What’s Truly Exploitable
Unlike traditional scanners or static analysis tools that flag hypothetical risks, offensive cybersecurity methods replicate real attackers' operations. The distinction between vulnerable and exploitable is key. In mature environments, security teams don’t need more alerts; they need clarity. Offensive testing delivers validated findings that are exploitable in context, allowing teams to prioritize what truly matters and reduce alert fatigue.
2. Reduces Mean Time to Fix
One of the hidden costs of traditional security testing is the time wasted sorting through false positives and vague findings. Offensive cybersecurity improves remediation velocity by generating concise, actionable results with proof-of-exploit, reproduction steps, and contextual metadata.
Platforms like Terra produce structured reports that integrate with developer workflows and CI/CD tooling, minimizing friction between AppSec and engineering and accelerating security feedback loops. Developers get the correct information, in the proper format, at the right time.
3. Surfaces Business Logic and Contextual Risks
Business logic flaws, such as order manipulation or multi-step abuse scenarios, are rarely caught by traditional tools, which are blind to application workflows and intent. These flaws are specific to the app’s design and use cases, not generic CVEs. Offensive testing, particularly with white-box or grey-box access, enables the simulation of real abuse paths based on how users (or attackers) interact with features.
4. Creates Compliance-Ready Results
Frameworks like SOC 2, ISO 27001, and PCI DSS increasingly require demonstrable evidence of control effectiveness. Offensive security provides this by showing how systems respond under actual attack conditions, not hypothetical checklists.
Moreover, offensive testing enables CISOs and security teams to communicate risk in operational terms (“this path led to customer data exfiltration within three steps”) rather than abstract CVSS scores. This level of clarity drives more informed security decisions, greater stakeholder buy-in, and stronger audit readiness.
7 Best Practices for Implementing Offensive Cybersecurity
1. Demand a Threat-Informed Testing Strategy
An effective offensive security program should simulate the tactics, techniques, and procedures most relevant to your threat landscape. Rather than relying on off-the-shelf CVE checks, look for partners or platforms incorporating adversary emulation frameworks (such as MITRE ATT&CK), recent threat intelligence, and company-specific attack paths.
This ensures your testing reflects your organization's actual risks, whether that’s credential stuffing in consumer-facing apps, API abuse in a SaaS app, or lateral movement across hybrid environments. As a leader, your role is to set the expectation that testing must reflect reality, not theoretical exposure.
2. Shift from Point-in-Time to Continuous Testing
Traditional pen tests offer a snapshot in time. But modern applications, particularly SaaS products and microservice-heavy platforms, change weekly, if not daily. Look for tools that provide continuous testing by embedding directly into the software development lifecycle. It’s important to note that not all “continuous” tools are the same. Many leverage shallow automation that fails to consider business logic.
Find tools that integrate into CI/CD pipelines and run intelligent, incremental tests that adapt to code changes and architectural shifts. This model reduces dwell time, increases test coverage, and enables a DevSecOps posture.
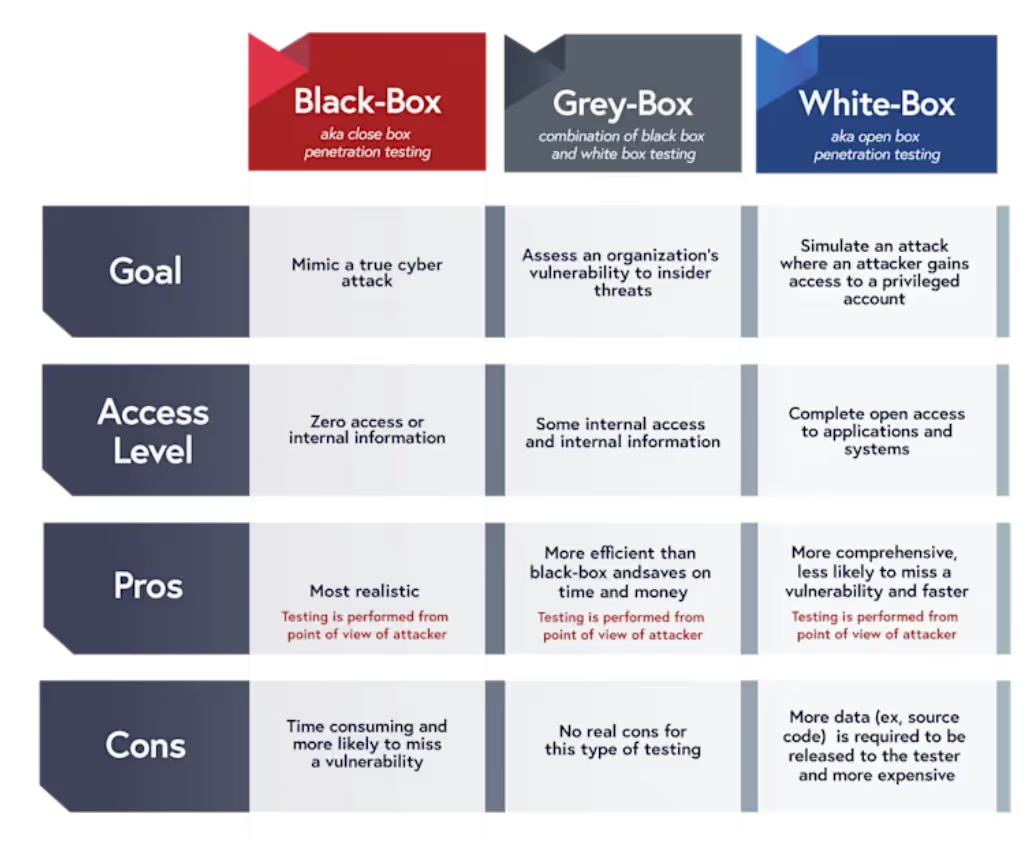
3. Use White-Box and Grey-Box Testing
While black-box testing has value in simulating external attackers with no context, it falls short when the goal is to uncover deep, context-specific flaws. White-box and grey-box testing allow offensive tools and teams to understand the application’s infrastructure, such as how data flows, how roles are structured, and how trust is extended across human and non-human identities.
Ensure your offensive security providers can run white-box or grey-box assessments. They should have appropriate access to source code, internal APIs, user roles, or architectural documentation. White and grey-box assessments enable higher fidelity testing and increase the chance of uncovering exploitable issues.
4. Simulate Business Logic Abuse and Custom Attack Paths
Business logic vulnerabilities require understanding the app’s intent, structure, and use cases. Your offensive security program should explicitly test for these abuse scenarios. Whether through manual red teaming, advanced automation, or a hybrid model, vendors must demonstrate their ability to model your business workflows and identify how a real attacker could misuse them.
Business logic is essential for customer-facing and revenue-critical applications, where offensive testing should be aligned with established SaaS security best practices. Consider, for example, e-commerce checkout flows, subscription management portals, booking engines, or any system that handles user permissions, transactions, or sensitive customer data.
5. Integrate Human Oversight
Even the most advanced autonomous systems have limitations. Your testing program should include skilled human testers who can filter out false positives and high-impact findings as part of the validation process. Beyond accuracy, the human-in-the-loop layer ensures that no disruptive or unsafe tests are executed in production environments and that findings are properly contextualized.
At Terra, this model is built in by design. AI agents conduct scalable, continuous tests while human experts oversee offensive actions, refine attack paths, and validate high-priority vulnerabilities. This hybrid model mirrors the structure of high-performing offensive security teams, where junior analysts handle breadth and senior operators focus on depth and impact.
6. Update Testing Scope Frequently
You should treat your scope as a living artifact that adjusts to application changes, user behavior analytics, and evolving threat landscapes. Ensure your team reviews it quarterly at minimum or in a continuous pull-mode when new exploitable vulnerabilities are introduced, and automatically re-evaluates it whenever there are significant changes to application architecture, new integrations, new externally exposed endpoints, or meaningful changes in data sensitivity or user access models.
Terra’s platform leverages continuous, change-based telemetry and integration metadata to evolve its testing scope in real time. As an adaptive tool, it eliminates the administrative burden of manually updating targets for organizations with sprawling app portfolios.
7. Push For Actionable Reporting
A core challenge in offensive testing is ensuring that findings don’t die in PDFs. Your provider or tool should build reports not just for auditors or leadership, but for the engineers responsible for remediation. That means:
- Prioritization based on exploitability and business impact
- Clear reproduction steps (with screenshots/video, payloads, and request logs)
- Practical, environment-specific recommendations
Bonus points for integration into your existing engineering tools, whether Jira, GitHub, or internal ticketing systems.
Putting OffSec to Work
Defensive controls are essential, but they’re not enough. You're relying on assumptions without knowing how your systems would withstand a real-world attack. Offensive cybersecurity reveals not just what’s theoretically vulnerable, but what’s exploitable, right now. It helps security leaders cut through noise, understand risk in business terms, and prioritize what matters.
Terra is the first agentic AI platform designed for offensive security. It continuously tests your entire application with real adversarial logic, adapts to code and architecture changes in real time, and prioritizes exploitable vulnerabilities based on business context.
Combining the scale of automation with the precision of human-in-the-loop expertise, Terra delivers full-context penetration testing that adapts to code changes, simulates real-world logic abuse, and provides developers and security engineers with actionable, risk-ranked findings. Explore more here.
Be the first to experience the future of security.
Secure your spot by leaving your email








